

Xint is an AI-powered web application security testing solution
that attacks your web environment like a real hacker,
using scenario-based black box penetration testing.
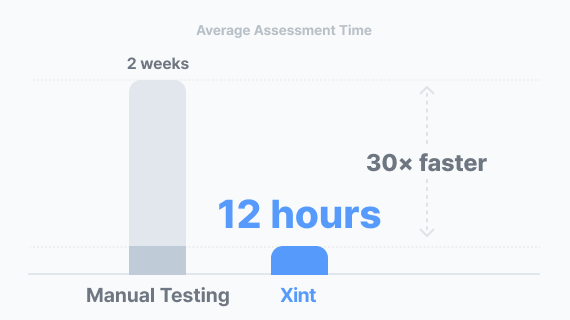
What used to take experts hours, Xint automatically maps in just a few hours.
Xint explores your app like a real user, mapping features, data flows, and logic to build a knowledge graph of how your application actually works.
This graph becomes the foundation of
Xint’s logic-aware security testing.
Xint automatically generates 30–50 advanced attack scenarios per URL, replicating the multi-step attack paths a human pentester would craft manually.
Connects vulnerabilities across multiple features to uncover multi-step business logic flaws.
Powered by Theori’s latest offensive research and real-world hacking expertise.
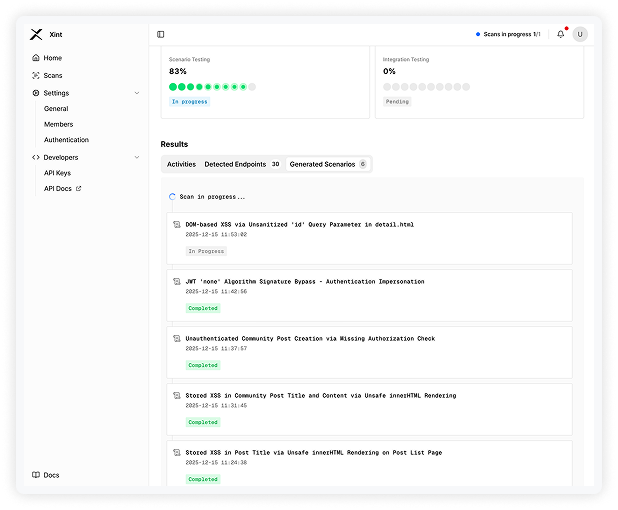
Xint automatically filters out false positives and reports only evidence-backed vulnerabilities, each delivered with reproducible PoC code.
Understands the purpose and context of each feature, correctly distinguishing real impact levels of similar-looking issues.
Provides clear explanations of confirmed vulnerabilities, supporting evidence, all with reproducible PoC code.

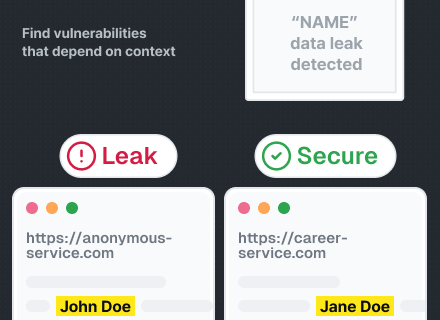
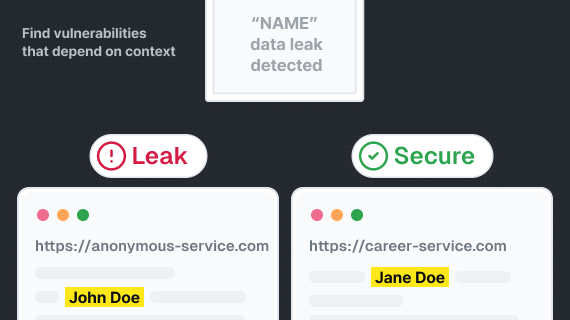
Find answers to common questions about Xint, including how our scanning works, what types of vulnerabilities we find, and key differentiators.
